Alarm Clock Smart Contract Exploited on Ethereum: Developing Story

Blockchain security firm PeckShield published the details of a new transaction fee refund exploit on the TransactionRequestCore smart contract belonging to the Ethereum Alarm Clock Project.
At press time, almost 24 hackers had looked to rob transaction owners by calling the transaction cancel function.
Smart contract refunds drained
The transaction fee then sent to the caller was very high compared to what the original transaction owners would have received if they requested the refund.
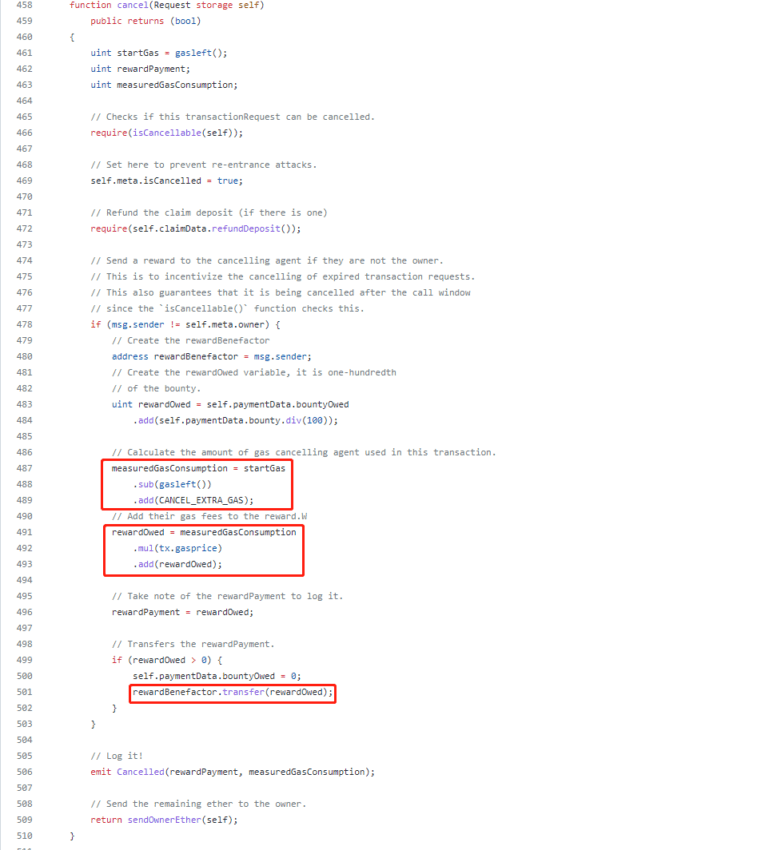
Source: Supremacy Inc.
As can be seen above, the purpose of the cancel function is to compute the owner’s gas cost and add a constant of 85,000 to that amount to refund them.
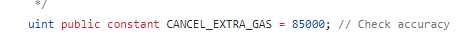
Source: Supremacy Inc.
Consequently, the hacker does not need to use more than 70,355 in gas to receive a refund greater than the original transaction fee. After that, they can pocket the difference.
Accordingly, one Twitter user, pyggie9, tweeted:
According to PeckShield, 51% of the bloated refund is paid out as profit to miners, increasing their Miner Extractable Value (MEV). So far, one of the beneficiaries has been an Ethereum validator using the liquid staking pool Lido Finance. Etherscan data reveals that the validator has reportedly received $158,000 (121 ETH) from contract 0xbb1d6b3be1396a4b5ccb8d061b302250bb2b73fd at block 15,782,459.
According to security company Supremacy Inc., hackers have stolen 204 ETH so far.
Miner extractable value refers to miners arranging transactions in blocks to maximize their profits. An accepted way to improve MEV returns is through a proposer/block-builder separation. A proposer in the Ethereum Virtual Machine can earn a tidy sum for sending blockspace to a cohort of reliable block builders.
Alarm clock operation
The Ethereum Alarm Clock project contains Ethereum transactions scheduled to occur at a future date. Transactions can be scheduled by people or smart contacts. Additionally, the EAC will enable TimeNodes to call transactions during a certain time frame.
The TransactionRequestCore smart contract involved in this latest exploit is four years old.
According to a recent report by research company Token Terminal, smart contract exploits are not easy to fix.
This hack is still active, and updates will be added soon.







 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  TRON
TRON  Bitcoin Cash
Bitcoin Cash  Chainlink
Chainlink  Polygon
Polygon  Litecoin
Litecoin  LEO Token
LEO Token  Dai
Dai  Hedera
Hedera  Stacks
Stacks  Ethereum Classic
Ethereum Classic  Cronos
Cronos  Stellar
Stellar  Cosmos Hub
Cosmos Hub  OKB
OKB  Maker
Maker  Theta Network
Theta Network  Monero
Monero  Algorand
Algorand  NEO
NEO  Gate
Gate  EOS
EOS  Tezos
Tezos  KuCoin
KuCoin  Synthetix Network
Synthetix Network  IOTA
IOTA  Bitcoin Gold
Bitcoin Gold  Tether Gold
Tether Gold  TrueUSD
TrueUSD  Enjin Coin
Enjin Coin  Zilliqa
Zilliqa  Ravencoin
Ravencoin  Holo
Holo  Siacoin
Siacoin  0x Protocol
0x Protocol  Qtum
Qtum  Basic Attention
Basic Attention  Ontology
Ontology  Decred
Decred  Dash
Dash  NEM
NEM  Zcash
Zcash  Lisk
Lisk  Waves
Waves  DigiByte
DigiByte  Numeraire
Numeraire  Status
Status  Nano
Nano  Hive
Hive  Pax Dollar
Pax Dollar  Steem
Steem  OMG Network
OMG Network  Huobi
Huobi  BUSD
BUSD  Ren
Ren  Bytom
Bytom  Bitcoin Diamond
Bitcoin Diamond  HUSD
HUSD  Kyber Network Crystal Legacy
Kyber Network Crystal Legacy  Energi
Energi  Augur
Augur