Hack Life: Top 4 Biggest Exploits in August and How They Got Access

Hack life: Unfortunately, hacks have become such a common occurrence that they are considered a part of everyday life. So much that we now compile monthly overviews of them.
According to one of the most recent reports by a data analysis platform Chainanalysis, vulnerabilities in cross-chain bridge protocols have posed the biggest security threat in the crypto industry; they now represent two-thirds of all hacks.
$263 million and counting
According to a blockchain security firm SlowMist Hacked, users lost around $263 million worth of cryptocurrency to hacks in August.
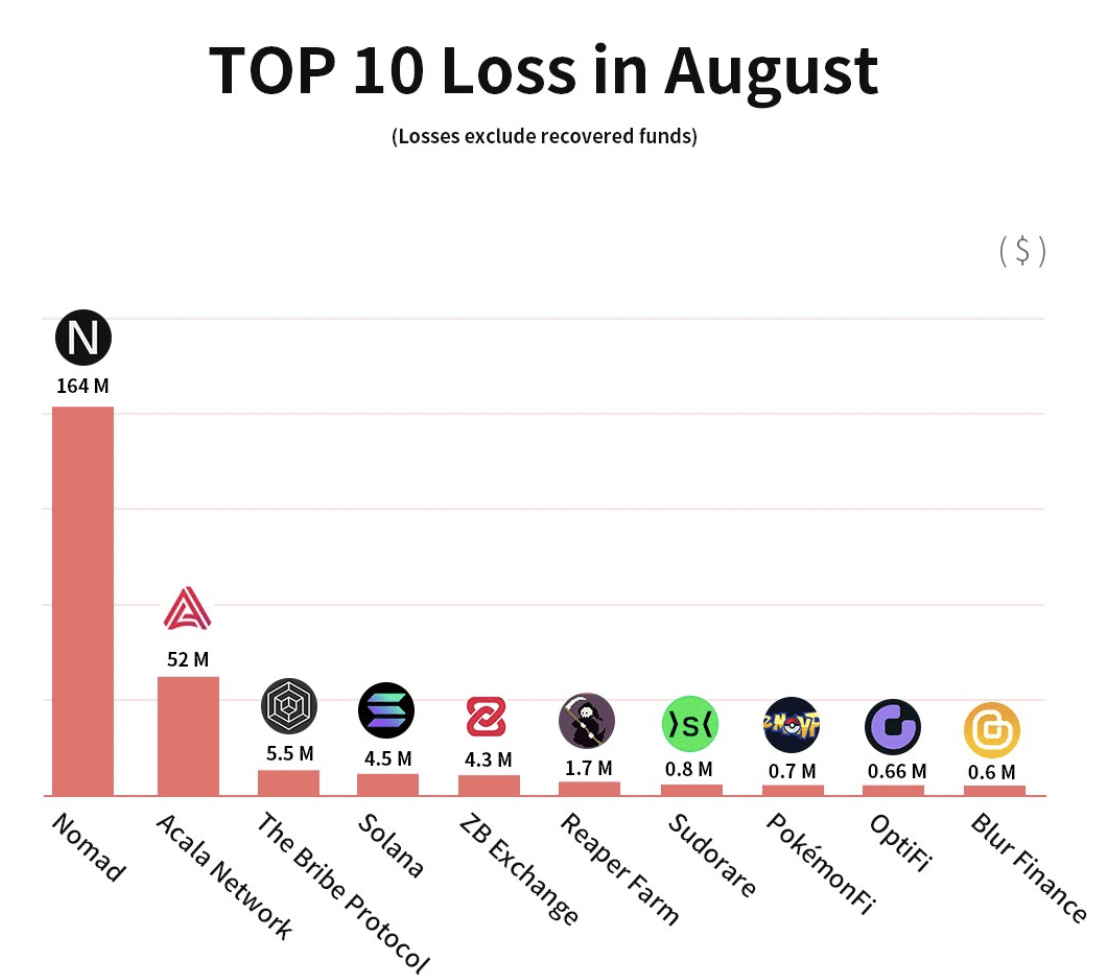
SlowMist Hacked
SlowMist Hacked stats show that the top 5 ways attacks were executed include contract vulnerabilities, rug pulls, Discord hack, frontend attack, and BGP hijacking.
This August kicked off with one of the most devastating attacks the industry has seen – the Nomad exploit.
Hack 1: Nomad
Assets stolen: $200 million
The Nomad bridge exploit is a devastating attack that led to $200 million worth of cryptocurrency being stolen from users’ accounts on Aug. 1. What drew even more attention to the hack is the number of attackers involved in the incident – 300 unique addresses. Some of the hackers even tried to impersonate Nomad’s employees to access more funds.
The exploit became possible due to a recent smart contract upgrade. “It turns out that during a routine upgrade, the Nomad team initialized the trusted root to be 0x00. Unfortunately, in this case, it had a tiny side effect of auto-proving every message,” one of the security analysts noted.
The platform later established a 10% bounty program, offering the hackers to return 90% of the funds they stole, leaving the 10% to themselves.
As of now, only $36 million has been returned, while one of the wallets connected to the exploit recently transferred $7.5 million worth of cryptocurrency to an unknown wallet address.
Hack 2: Acala Network
Assets stolen: $52 million
On Aug. 14, a Twitter user 0xTaysama noticed suspicious activity on a Polkadot (DOT)-based DeFi platform Acala, suggesting that there might be a hack. They also identified a potential reason behind the attack, “a bug in the iBTC/AUSD pool.”
The hacker managed to exploit the bug to mint 1.2 billion aUSD, the native token of the Acala Network. This prompted a 99% fall in the token’s price and consequent depegging, falling to $0.60 and hovering around $0.90.
The platform’s developers said the bug appeared as a result of the misconfiguration of the iBTC/aUSD liquidity pool. The liquidity pool went live earlier on that same day. Acala suspended the protocol shortly after the attack, disabling the transfer of the stolen assets.
On-chain analysts pointed out that the other users might have used the bug and the attack to steal thousands of dollars in DOT.
Hack 3: Solana
Assets stolen: $5.8 million
Around 8,000 hot mobile wallets fell victim to the attack that drained $5.8 million in SOL, USDC, and others on Aug. 2-3. The wallets connected to the Solana (SOL)ecosystem included TrustWallet, Phantom, and Slope.
The attackers seemed to have gained access to the users’ signatures, which could indicate some third-party service might have been compromised through a supply chain attack.
Solana developers believe that the hack was initiated in a software popular among network users.
A vulnerability in a Solana mobile wallet Slope seemed to be the reason behind the hack. According to the official Solana Status Twitter, “this exploit was isolated to one wallet on Solana, and hardware wallets used by Slope remain secure.”
The developers reminded the users about the reliability and security advantages of cold wallets over hot ones to avoid future security vulnerabilities.
Be[in]crypto reached out to Solana but hasn’t received a response.
Hack 4: ZB.com
Assets stolen: $4.8 million
Ironically, a crypto exchange that positioned itself as “the world’s most secure digital exchange exchange” and manages over $1 billion in trades on a daily basis was hacked for $4.8 million on Aug. 2.

The 20 digital assets, including USDT, MATIC, AAVE, and SHIB, were moved from the exchange and sold shortly after for Ethereum on different decentralized exchanges, PeckShield data shows.
The exchange suspended withdrawals and deposits, first describing it as “temporary maintenance” and then “the sudden failure of some core applications,” which led many in the community to believe it might be an exit scam.
Basic Protection
With so many attacks and exploits happening in the industry, it is vital to remember the basic protection steps. These include choosing a cold wallet over a hot one, never revealing a recovery phrase and keeping it in different places in hard copies, using two-factor authentication, being careful and double checking the links and emails before clicking on them.






 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  USDC
USDC  TRON
TRON  Dogecoin
Dogecoin  Cardano
Cardano  Bitcoin Cash
Bitcoin Cash  Monero
Monero  Chainlink
Chainlink  LEO Token
LEO Token  Stellar
Stellar  Zcash
Zcash  Litecoin
Litecoin  Hedera
Hedera  Dai
Dai  Cronos
Cronos  OKB
OKB  Tether Gold
Tether Gold  Ethereum Classic
Ethereum Classic  KuCoin
KuCoin  Cosmos Hub
Cosmos Hub  Gate
Gate  Algorand
Algorand  VeChain
VeChain  Dash
Dash  Stacks
Stacks  Tezos
Tezos  TrueUSD
TrueUSD  IOTA
IOTA  Decred
Decred  Theta Network
Theta Network  Basic Attention
Basic Attention  NEO
NEO  Synthetix
Synthetix  Qtum
Qtum  0x Protocol
0x Protocol  Ravencoin
Ravencoin  Zilliqa
Zilliqa  DigiByte
DigiByte  Nano
Nano  Siacoin
Siacoin  Numeraire
Numeraire  Enjin Coin
Enjin Coin  Waves
Waves  Ontology
Ontology  Status
Status  Hive
Hive  BUSD
BUSD  Lisk
Lisk  Pax Dollar
Pax Dollar  Steem
Steem  Huobi
Huobi  OMG Network
OMG Network  Bitcoin Gold
Bitcoin Gold  NEM
NEM  Augur
Augur