‘Address Poisoning’ Attack Sees Scammer Make Off With $1.3M in ARB Tokens

Initially reported as a «lucky» Arbitrum airdrop recipient, one crypto address appears to have actually scammed out over 600 different crypto wallets for more than 930,000 ARB tokens.
Blockchain intelligence firm Arkham confirmed with Decrypt that they too have identified that the address “belongs to a hacker who is sweeping funds from Arbitrum users.”
A closer look at the specific address’s transactions reveals that it received 933,365 ARB tokens from a different Arbitrum address on March 24, a day after the layer-2 network’s highly-anticipated airdrop. ARB is the native governance token behind the layer-2 scaling solution for Ethereum called Arbitrum.
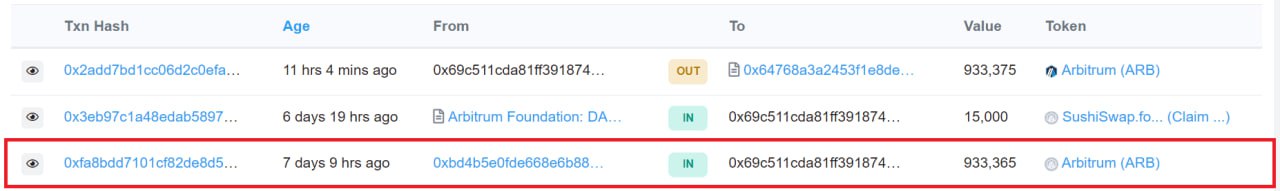
Transfer of 933,365 ARB tokens on-chain. Source: Arbiscan.
The source of those tokens is another contract whose creator is tagged as “Fake_Phishing18” on Arbitrum’s blockchain explorer.
Independent on-chain researcher 0xKnight also confirmed that he found victim reports of the hack. Users complained that their ARB tokens had been “auto-claimed” to the hacker’s wallets.
Ethereum smart contract developer Brainsy signaled the malicious contract created by “Fake_Phishing18” on March 24 as well. They said that interacting with the contract creates an additional transaction request that appears as if it’s from the sender’s wallet but instead is a phishing attack.
Watch out for this fake Arbitrum contract out there.
When I make a send the fake contract also makes a «transaction» that appears like its from my wallet. I assume to get me to interact with the contract. Stay safe out there. pic.twitter.com/ygGOddlTGU
— Brainsy (@BrainsyEth) March 24, 2023
MetaMask has warned against this sort of attack and termed it “address poisoning.”
It is an attempt where attackers poison the address list of users’ wallets by sending arbitrary transactions from addresses that closely resemble those with which the user has already interacted.
In this case, the attacker appears to have used both a phishing attack through a malicious smart contract and address poisoning, with Brainsy indicating that it makes the transaction look “like it’s from [the users’] wallet.”
The “Fake_Phishing18” tag is also associated with another address called “Fake_Phishing47” which deployed a fake ARB token contract on March 21.
The image below shows that the “Fake_Phishing18” tagged account created the contract for the fake ARB tokens and then transferred ownership to “Fake_Phishing47.”
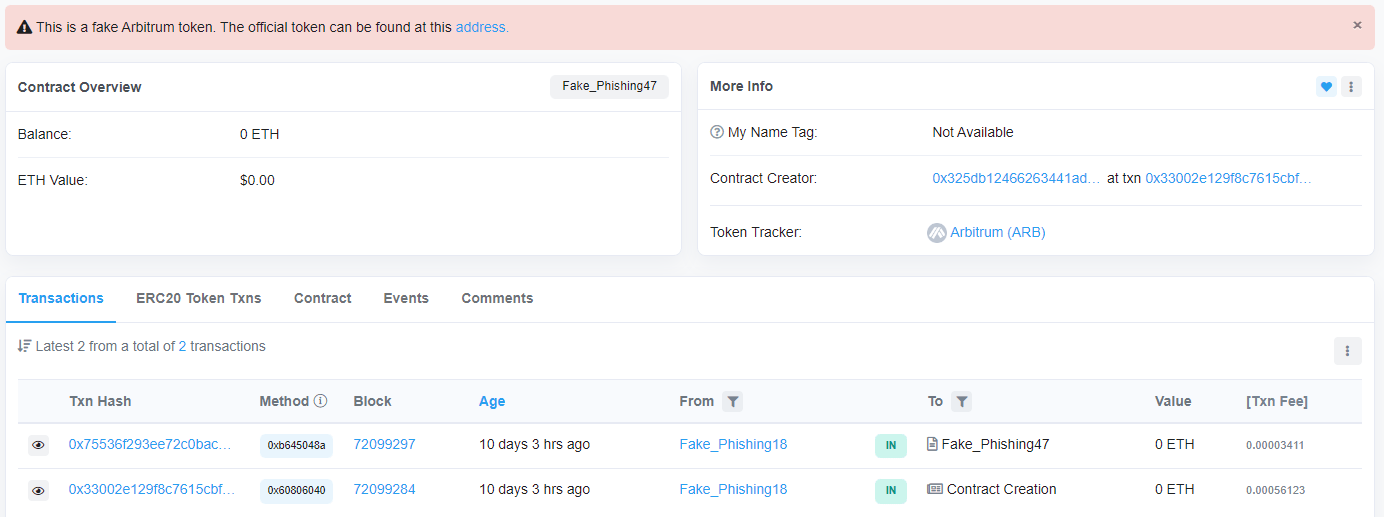
Contract details for fake ARB tokens. Source: Arbiscan
The same may have created a fake Aribtrum claiming site that if users interacted with the website, it would give the hacker control over the user’s wallets.
For instance, there was at least one identical webpage to the Arbitrum Foundation’s claim website circulating in some social media groups on the day of the airdrop.
The fake website claimed ARB tokens on the user’s behalf and transferred them to their wallets. The only subtle difference between them is that the original website has a countdown for when the claiming process will end.







 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  Chainlink
Chainlink  TRON
TRON  Bitcoin Cash
Bitcoin Cash  Polygon
Polygon  Litecoin
Litecoin  LEO Token
LEO Token  Dai
Dai  Ethereum Classic
Ethereum Classic  Hedera
Hedera  Cosmos Hub
Cosmos Hub  Cronos
Cronos  Stellar
Stellar  Stacks
Stacks  OKB
OKB  Monero
Monero  Maker
Maker  Theta Network
Theta Network  Algorand
Algorand  NEO
NEO  Gate
Gate  KuCoin
KuCoin  Synthetix Network
Synthetix Network  Tezos
Tezos  EOS
EOS  IOTA
IOTA  Bitcoin Gold
Bitcoin Gold  Tether Gold
Tether Gold  Enjin Coin
Enjin Coin  TrueUSD
TrueUSD  0x Protocol
0x Protocol  Zilliqa
Zilliqa  Holo
Holo  Ravencoin
Ravencoin  Siacoin
Siacoin  Zcash
Zcash  Qtum
Qtum  Basic Attention
Basic Attention  Dash
Dash  NEM
NEM  Decred
Decred  Ontology
Ontology  Waves
Waves  Lisk
Lisk  Numeraire
Numeraire  DigiByte
DigiByte  Nano
Nano  Pax Dollar
Pax Dollar  Status
Status  Hive
Hive  Steem
Steem  OMG Network
OMG Network  Huobi
Huobi  Ren
Ren  BUSD
BUSD  Bytom
Bytom  Kyber Network Crystal Legacy
Kyber Network Crystal Legacy  Bitcoin Diamond
Bitcoin Diamond  Energi
Energi  HUSD
HUSD  Augur
Augur