Explainer: Best Practices to Secure Your Precious Crypto Coins and NFTs

Crypto Safety Is YOUR Responsibility
Cryptocurrencies and blockchain technology promote financial freedom. They empower us to control our finances and be our own banks. However, it means we must take responsibility for the safety of our funds to prevent them from getting into the wrong hands. One incentive that should make us serious about crypto security is this: It is difficult to recover lost crypto. So it’s better not to lose them in the first place.
While it is probably impossible to eliminate all risk vectors, crypto security aims to reduce the risks to minimum level possible. Whether you are an active crypto trader, investor, or just storing your wealth in crypto assets, here is a collection of helpful strategies that can help you keep your coins and Non-Fungible Tokens (NFTs) safe.
Use a Unique, Strong Password

Source
- Use one password for each platform you’re on. If your password gets compromised, that ensures the risk is limited to only one platform.
- Make your password as strong as possible by using a random combination of upper case, lower case, numbers and special characters. Change your passwords regularly. An example of a strong password is hjD2iR#JnXpPkQ@4r&4t5. Though most strong passwords are not easy to commit to memory, encrypted password managers like LastPass can make the generation and retrieval of strong passwords for all your accounts more convenient.
Choose Your Trading Platform Carefully

Source
Whether you are trading on a Decentralized Exchange (DEX) like PancakeSwap or a Centralized Exchange (CEX) like Binance, you should use platforms that you trust.
- If you choose to trade on a CEX, use one that is compliant with laws and regulations, has a reasonable level of consumer protections, and has a strict “Know Your Customer” (KYC) policy.
- Add an extra layer of security to your accounts by activating multi-factor authentication.
- It is also good advice to trade on platforms with a verifiable Secure Asset Fund for Users (SAFU), ensuring you can recover a good amount of your funds if hackers steal users’ assets from the CEX.
- While many users find DEXes and
- On the other hand, many users find using decentralized platforms like DEXes and Decentralized Finance (DeFi) protocols to be convenient, they are typically not regulated and may not have as robust a security architecture as a CEX. At minimum, you should use a DEX whose smart contract has been reviewed by reputable security auditors, like Certik.
Use a Burner Wallet to Mint Your NFTs

Source
A burner wallet is a wallet created for temporary use that is separate from a user’s main wallet and is useful when the user wants to interact with platforms of uncertain security status. For example, if you want to mint an NFT and are not sure of the audit status of the minting platform, do not mint it with your main wallet. Instead, create a new wallet and transfer the funds needed to cover the mint to it. After minting, you can transfer the NFT to your main wallet and discard the burner. Using a burner wallet will protect the bulk of your assets if you interact with a scam NFT platform.
Review Your Wallet’s Permissions Regularly

Source
- DEXes and NFT minting platforms usually request permission to let their smart contracts interact with a user’s wallet. Many of these permissions give unlimited access privileges to those contracts, which a bad actor can use as a backdoor to your wallet. They are also sticky and remain active after a user’s transaction ends. Make it a regular habit to remove the access permissions on your wallet. You can use revoking tools like BscScan, Etherscan, etc.
- Some wallets like Metamask allow users to edit the level of approval given to a smart contract. The feature enables users, at the point of approving a transaction, to set the maximum amount of crypto assets on a user’s wallet that the smart contract can spend. So if I have 500 BNB, for example, I can limit the smart contract’s spending limits to 1 BNB only. It’s a terrific way of creating a firewall around your wallet. HERE is a good guide by Twitter user CryptoCat, which shows how to modify Metamask token approvals.
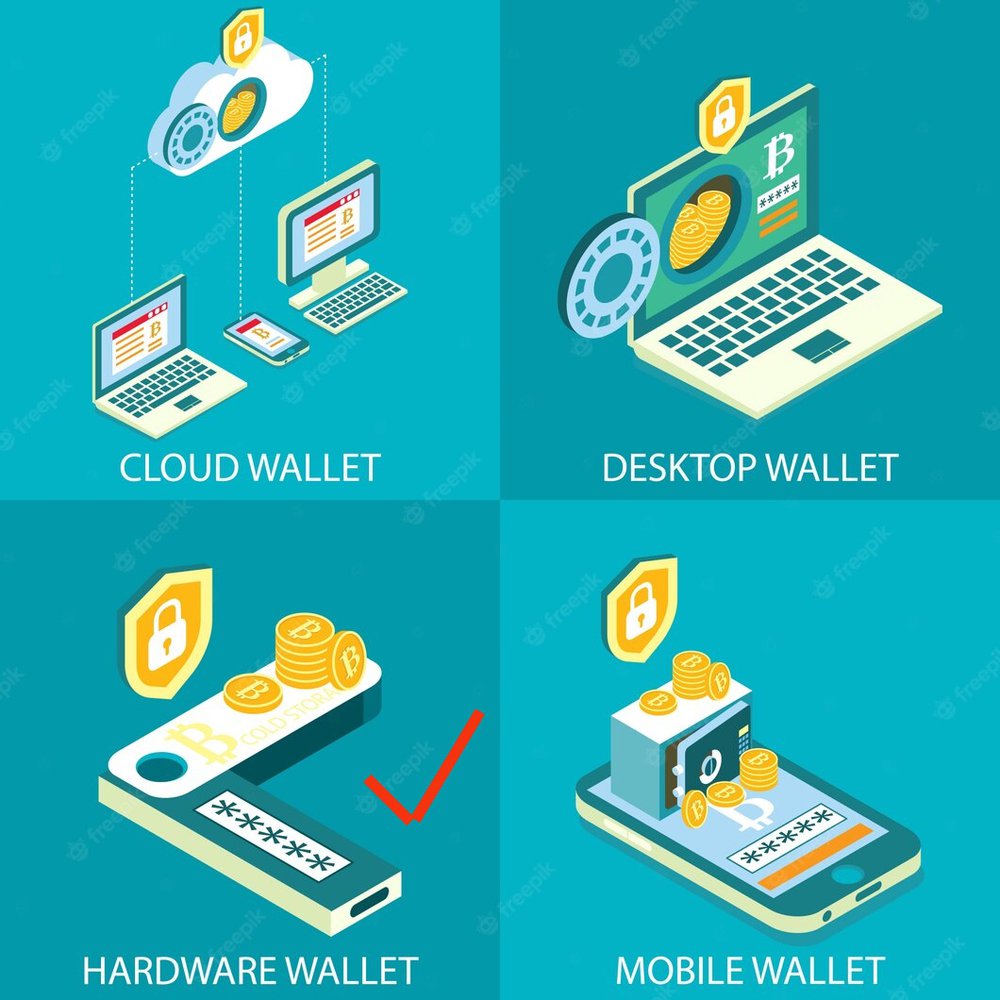
Store Your Crypto Assets and Keys Offline
Source
No one can access your crypto wallet without your private key or seed phrase. Hackers need an internet connection to attempt hacking into the wallets of their victims. Hence,
- The safest way to store your crypto, keys, and seed phrases is on an offline device.
- Do not save your keys or phases as a contact or screenshot on your internet-enabled phone, laptop, email account, etc. Instead, keep your keys in a secure offline location, such as a hardware wallet.
While it may be hard to give guarantees in crypto, hardware wallets are one of the safest crypto offline storage systems. There are no known incidents where a hardware wallet got compromised via an internet hack resulting in the theft of the owner’s crypto assets.
Scan Your Email Address Regularly
Source
Sometimes, data breaches — like the one that affected 500 million Yahoo users, expose users’ email addresses and passwords to the wrong eyes. Avoid using the same passwords you used for your email accounts as registration passwords on crypto platforms. Else, such breaches could put your crypto accounts at risk. You can scan your email addresses HERE to see if they have been exposed in any previous data breach. If exposed, change your passwords immediately.
Maintain a Low Profile
Crypto thieves can sometimes move from stalking their targets online to offline, real-world robbery attempts. Therefore, protect yourself in the real world by not revealing details about your crypto holdings online or offline. Also, avoid posting information about your offline identity and location on online platforms.
Beware of Phishing

Source
Phishers are criminals who try to convince or trick their victims into releasing sensitive information about themselves, such as passwords and seed phrases. Here are some things you can do to avoid falling victim:
- Avoid logging into your crypto accounts on public computers, as an attacker can capture your login details with a keylogger.
- Hackers easily infiltrate public WiFi because they are generally not configured with solid network security. So avoid using them to access your crypto accounts.
- Always cross-check the address of every crypto website you visit to be sure it is not a clone. Also, check to ensure the site is secure. The address should begin with “https” and have a padlock sign if it’s a secure site. If the website is not secure, avoid using it.
- Beware of unsolicited emails. Do not click on links of unknown origin. Ignore messages you receive on Discord, Telegram, etc., about crypto or NFT schemes if you don’t know or can’t verify the sender.
- Scammers often clone fake versions of crypto wallets and apps, which they use to steal sign-in details. So make sure to use only verified official links when downloading crypto apps.

Source
Store Your Crypto in Multiple Wallets
If you have a significant quantity of crypto, you could consider splitting it and saving your assets in more than one wallet. Spreading your holdings in multiple wallets will protect you from a total loss of funds if one of the wallets gets hacked.
The tips in this article will give anyone a good start in crypto security. However, crypto criminals continually evolve their tactics. Therefore, the best security attitude is to view every crypto website you visit and every Decentralized Application (dApp) you interact with as a potential security risk. That way, you will always be alert and more likely to perform due diligence.







 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  TRON
TRON  Bitcoin Cash
Bitcoin Cash  Chainlink
Chainlink  Polygon
Polygon  Litecoin
Litecoin  LEO Token
LEO Token  Dai
Dai  Ethereum Classic
Ethereum Classic  Hedera
Hedera  Cronos
Cronos  Stacks
Stacks  Cosmos Hub
Cosmos Hub  Stellar
Stellar  OKB
OKB  Maker
Maker  Monero
Monero  Theta Network
Theta Network  Algorand
Algorand  NEO
NEO  Gate
Gate  KuCoin
KuCoin  Tezos
Tezos  EOS
EOS  Synthetix Network
Synthetix Network  IOTA
IOTA  Bitcoin Gold
Bitcoin Gold  Tether Gold
Tether Gold  TrueUSD
TrueUSD  Zilliqa
Zilliqa  Enjin Coin
Enjin Coin  Holo
Holo  Ravencoin
Ravencoin  0x Protocol
0x Protocol  Siacoin
Siacoin  Qtum
Qtum  Basic Attention
Basic Attention  Dash
Dash  NEM
NEM  Zcash
Zcash  Decred
Decred  Ontology
Ontology  Lisk
Lisk  Waves
Waves  DigiByte
DigiByte  Nano
Nano  Status
Status  Numeraire
Numeraire  Pax Dollar
Pax Dollar  Hive
Hive  Steem
Steem  Huobi
Huobi  OMG Network
OMG Network  BUSD
BUSD  Ren
Ren  Bitcoin Diamond
Bitcoin Diamond  Bytom
Bytom  Kyber Network Crystal Legacy
Kyber Network Crystal Legacy  HUSD
HUSD  Energi
Energi  Augur
Augur