Cross-chain Bridge: The Development And Hidden Worries

Token Terminal, an analyzing tool, once published amazing statistics. From 2021 to 2022, more than $2.5 billion dollars in encrypted assets were stolen on the cross-chain bridge, more than double the amount taken in the previous two years.
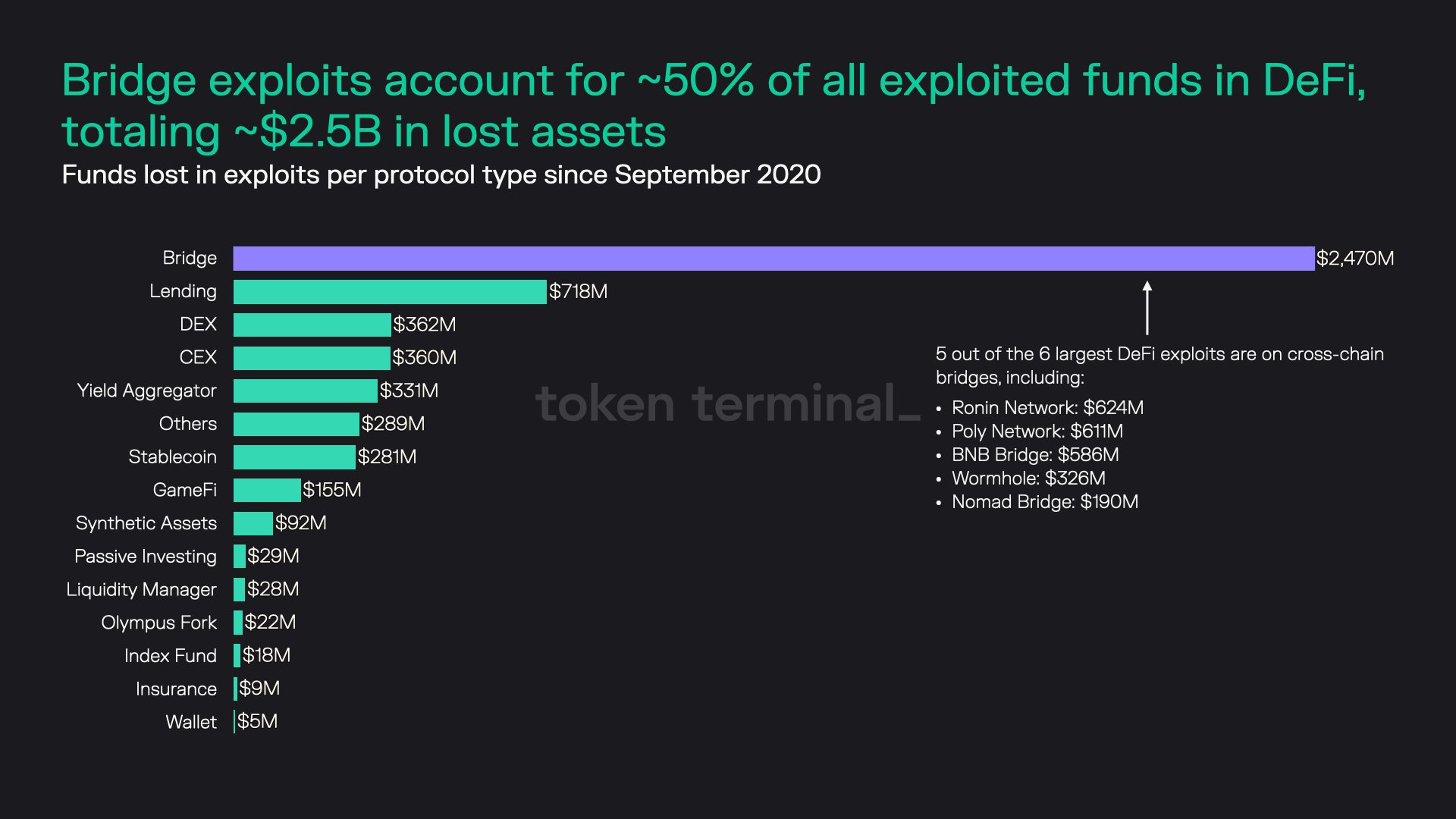
Despite developers’ efforts to strengthen the bridge’s security, discussions on the Uniswap DAO forum early this year revealed that the cross-chain bridge still exposed various security issues.
Uniswap DAO, the autonomous organization of the decentralized exchange Uniswap, suggested in December last year to deploy Uniswap v3 on BNB Chain and chose a cross-chain bridge protocol to deploy the fund’s bridge.
As a result, as discussions progressed, participants discovered that no cross-chain bridge protocol could match everyone’s financial security needs.
What is a cross-chain bridge?
A cross-chain bridge, as the name implies, is a mechanism that connects two blockchains. Data and money on the two chains can be transferred from one to the other using the cross-chain bridge. In the most basic case, users can transmit USDC from Ethereum to Binance Smart Chain through a cross-chain bridge.
On the surface, money is flowing across the bridge. Yet, each blockchain, including. Ethereum and Binance Smart Chain, is closed, with distinct network structures and databases. In essence, the USDC before the transfer results from the USDC after the transfer.
Readers can learn more about. Layer 2 blockchain bridges here.

The functioning of the cross-chain bridge to accomplish the cross-chain transfer of cash is as follows: Using the preceding example, before the user transfers, the bridge will first lock the USDC on the Ethereum side, and then when the user clicks the transfer, the currency will create another USDC fund of the same amount on the An Smart Chain.
If the user wishes to return funds, Binance Smart Chain will delete the newly minted “USDC” and unlock the USDC on the Ethereum side. Hence, in theory, the cross-chain bridge does not really shift USDC from one chain to another. But, from an application standpoint, this can already suit the great majority of customers’ needs for transferrin payments.
Bridges can fail
The cross-chain bridge secures cash at one end while minting funds at the other. In general, appropriate verifiers are in charge of checking. Yet, you can steal a lot of money if you scam the verification on any one end. On one end, monies are not locked, but new funds are coined on the other. Alternatively, the initial money was not lost while transferring back, but this end of funds was successfully unlocked.
In other words, if the cross-chain bridge is taken, the monies are not only not lost, but an additional fund is created out of thin air. Binance Chain, for example, was taken.
Alternatively, instead of defrauding the verifier, steal straight from the verifier directly because the money locked by the user is held in the multi-signature wallet handled by the verifier. One example is the Ronin cross-chain bridge.
Ronin is a side chain created specifically for the blockchain game Axie Infinity, which makes it easier for players to enjoy the game, but the funds must be settled on Ethereum, therefore, the cross-chain bridge was created.
The cross-chain bridge verifier consists of nine verification nodes, with at least five node signatures necessary to validate the transaction. Even if only one node is hacked, the hacker will be unable to get the stolen cash.
As a consequence, Sky Mavis, the creator of Axie Infinity, had the keys to four of the nine verification nodes. After successfully transferring $620 million in crypto assets in wallets after hacking into Sky Mavis, the hacker simply attacked the final third-party node to gain verification authority.
Even Sky Mavis was ignorant of the theft until many days later. The current scenario could not be brought up until the user reported it, and Sky Mavis was startled that it had lost $620 million.
A new cross-chain bridge protocol has been developed
After a series of hacks on cross-chain bridges based on multi-signature verification, someone created a new cross-chain bridge project.
LayerZero
LayerZero replaces validators at both ends of the bridge with two servers. An “oracle” is the name given to the initial server. If the user locks the money, the Oracle machine will pass the locked funds’ block information to another chain where the monies will be moved.
A “relay” is the name given to the second server. When the user locks the money, the relay will transmit proof to the other chain to establish that the oracle is correct and that the locked funds are truly in that block.
But the oracle and the relay are unrelated, and there is no collusion. In this manner, hackers cannot evade verification in a single step and take cash.
LayerZero’s default oracle is Chainlink, and it includes default relayers for application developers. Developers can even tweak the development of these two servers if they choose.
Celer
Celer verifies if encrypted assets are locked using POS verification nodes and the proof-of-stake network. The verification will succeed if two-thirds of the verifiers feel that the user’s locked funds are legitimate.
According to Celer co-founder Mo Dong, the protocol also has a technique akin to optimistic Rollup. A waiting period is required for the transaction. At this time, the transfer of cash will be halted if a validator’s information is discordant with two-thirds of the nodes.
So, who is a validator? Mo stated that there are 21 validators in total, all of whom are credible PoS validators. What is its identity? Binance, Everstake, InfStones, Ankr, Forbole, 01Node, OKX, HashQuark, RockX, and more are examples.
Wormhole
Wormhole is to add 19 persons if 5 are insufficient, rely on these 19 verifiers to avoid fraudulent transactions, and 13 of the 19 verifiers must agree before cash can be transmitted.
Wormhole argues the network is more decentralized and has more credible verifiers than its competitors, including high-quality POS verifiers like Staked, Figment, Chorus One, and P2P.

Debridge
Debridge is a POS network with 12 verifiers, and only 8 of them agree that the fund transfer is legal. Validators who attempt to pass fraudulent transactions will be punished.
All deBridge validators “are expert infrastructure providers who validate numerous different protocols and blockchains,” according to DeBridge co-founder Alex Smirnov, and “all validators incur reputational and financial risks.”
Security and decentralization concerns
Yet, during the Uniswap DAO debate, all of these protocols were questioned about security and decentralization.
App developers have more control over LayerZero
LayerZero has been attacked for masquerading as a two-person multi-signature verification, and it also places verification in the hands of application developers. It has been discovered that the LayerZero oracles and relays can even be bypassed if hackers take control of the application developer’s computer system.
Others attacked the relay for being able to show the validity of the oracle but not the relay itself, and the relay itself is still closed source, making it hard for the public chain project party to swiftly construct its own relay.
The Celer security model is not without problems
Celer was chosen as Uniswap’s official cross-chain bridge in the inaugural voting by Uniswap DAO. As a result, the Celer security concept was significantly questioned when tested.
Celer features an upgradable MessageBus smart contract controlled by five multi-signature verifiers, and hackers may control the entire protocol if they have three of the signatures.
According to Mo, the co-founder of Celer, the contract is managed by four institutions: InfStones, Binance Staking, OKX, and Celer Network. He feels that the MessageBus contract should be kept in order to solve any potential future problems.
But this is clearly not entirely compelling.
Wormhole does not have a punishment system
Wormhole has been chastised for lacking a method to penalize fraudulent validators and for purportedly having lower transaction volumes than initially stated.
According to Mo Dong, the inventor of Celer, more than 99% of Wormhole’s transactions come from the Python side. When it was removed, there were just 719 transactions per day in the previous 7 days.
DeBridge has few complaints about it, not because it is weak, but because no one is paying attention to it at all. Most participants in the debate believe that Celer, LayerZero, and Wormhole are the most popular.
After reaching the critical step of selecting a cross-chain bridge, the Debridge team began to push for the use of a multi-bridge solution.
Can security be guaranteed by cross-chain bridges?
Transferring cash to another cross-chain bridge address is a frequent way for users to lock funds. If the verifier’s multi-signature wallet is granted the power to withdraw money, criminals who obtain control of the multi-signature wallet can withdraw tokens without the user’s awareness.
In essence, this is centralization disguised, and the voice delivered is intended to persuade people of the authority’s nature rather than a decentralized system.
On the other hand, the proof-of-stake verification network is incredibly complicated, and it is completely feasible that faults will be difficult to resolve in a timely way. Moreover, in a decentralized network, bridges cannot be fixed by hard forks, which is why Celer has concerns.
As a result, developers of cross-chain bridges will continue to face trade-offs, such as whether to hand over the upgrade to authorities who could be hacked or even do evil, or to achieve true decentralization that cannot be upgraded due to the enormous pressure of not being able to close the loopholes.
At the moment, as tens of billions of dollars continue to collect on the cross-chain bridge and as the encryption ecosystem develops, the question of how to establish a balance between security and decentralization for the cross-chain bridge will only grow more pressing.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.






 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  Dogecoin
Dogecoin  USDC
USDC  Cardano
Cardano  TRON
TRON  Chainlink
Chainlink  Stellar
Stellar  Hedera
Hedera  Bitcoin Cash
Bitcoin Cash  LEO Token
LEO Token  Litecoin
Litecoin  Cronos
Cronos  Ethereum Classic
Ethereum Classic  Monero
Monero  Dai
Dai  Algorand
Algorand  Stacks
Stacks  Cosmos Hub
Cosmos Hub  OKB
OKB  Theta Network
Theta Network  Gate
Gate  Maker
Maker  KuCoin
KuCoin  Tezos
Tezos  IOTA
IOTA  NEO
NEO  Polygon
Polygon  Synthetix Network
Synthetix Network  Zcash
Zcash  Tether Gold
Tether Gold  TrueUSD
TrueUSD  Dash
Dash  Holo
Holo  Enjin Coin
Enjin Coin  Zilliqa
Zilliqa  0x Protocol
0x Protocol  Basic Attention
Basic Attention  Qtum
Qtum  Ravencoin
Ravencoin  Siacoin
Siacoin  Bitcoin Gold
Bitcoin Gold  Decred
Decred  NEM
NEM  DigiByte
DigiByte  Ontology
Ontology  Nano
Nano  Huobi
Huobi  Status
Status  Waves
Waves  Lisk
Lisk  Numeraire
Numeraire  Hive
Hive  Steem
Steem  Pax Dollar
Pax Dollar  BUSD
BUSD  OMG Network
OMG Network  Ren
Ren  Bitcoin Diamond
Bitcoin Diamond  Bytom
Bytom